Now days, smartphones and tablets are most the popular gadgets. If we
see recent stats, global PC sale has also been decreasing for the past
few months. The reason behind this is that people utilize tablets for
most of their work. And there is no need to explain that Android is
ruling global smartphone and tablet markets. Android is most popular
mobile OS with more than 60% market share.
So, companies are now focusing on bringing their software as a mobile
app for Android. These apps include office apps, photo editing apps,
instant messaging apps and penetration testing apps. If you have an
Android smartphone, you can start your next penetration testing project
from your Android phone. There are few android apps that can turn your
Android device into a hacking device. Although, these apps have so many
limitations and can only be used for few specific tasks. You can never
get the same experience as you get with your PC. But smaller jobs can be
performed. Apps for penetration testers are not available widely, but
hackers can enjoy this platform in a better way. There are many
Wi-Fi hacking and sniffing apps available.
As we already said that Android is ruling smartphone and tablet
markets, developers are also creating more apps for Android devices.
This is the reason why the Android market has millions of apps. Like
websites, apps also need penetration testing to check for various
vulnerabilities. Security testing for Android apps will need to have a
penetration testing environment on your Android device.
Note:
- These apps are not for beginners because expertise is needed on the Android platform.
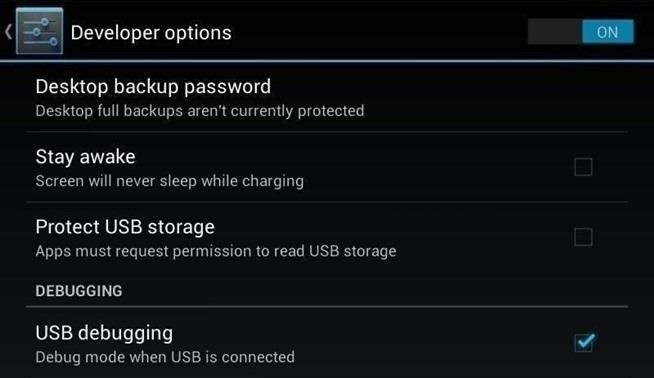
- Most of the apps work on Rooted Android devices. So root your
Android device first. If you are not sure how to do it, learn how to by,
reading one of the many sites available to help with this process.
- You will lose your device’s warranty if you root it, so think twice before proceeding.
- These apps can also harm your Android device. So please try these apps at your own risk.
In this detailed post, we will see various apps for web application
penetration testing, network penetration testing, sniffing, networking
hacking and Android apps penetration testing.
Android apps for Penetration testing
1. dSploit
dSploit is a nice Android network penetration testing suit. It comes
with all-in-one network analysis capabilities. Like most of the other
penetration testing tools, it also comes for free. So, you can download
and use this app on your Android device and perform network security
testing. It has various pre-complied modules to use. The app is designed
to be very fast, handy and easy to use, it’s just point and click.
dSploit supports all Android devices running on Android 2.3
Gingerbread or higher, and you also need to root your device. If you are
newbie, we will never recommend you to use the app if you don’t know
how to root your Android device. After rooting your device, you need to
install BusyBox Installer. Download BusyBox from Google Play Store:
https://play.google.com/store/apps/details?id=com.jrummy.busybox.installer&hl=en
Then download the app from the link given below.
App is available on github:
https://github.com/evilsocket/dsploit/downloads
These are the available modules in the app.
- RouterPWN
- Trace
- Port Scanner
- Inspector
- Vulnerability Finder
- Login Cracker
- Packet Forger
- MITM
2. Network Spoofer
Want to learn more?? The InfoSec Institute
Web Application Penetration Testing Boot Camp
focuses on preparing you for the real world of Web App Pen Testing
through extensive lab exercises, thought provoking lectures led by an
expert instructor. We review of the entire body of knowledge as it
pertains to web application pen testing through a high-energy seminar
approach.
The Web Application Penetration Testing course from InfoSec Institute is
a totally hands-on learning experience. From the first day to the last
day, you will learn the ins and outs of Web App Pen Testing by attending
thought provoking lectures led by an expert instructor. Every lecture
is directly followed up by a comprehensive lab exercise (we also set up
and provide lab workstations so you don't waste valuable class time
installing tools and apps). Benefits to you are:
- Get CWAPT Certified
- Learn the Secrets of Web App Pen Testing in a totally hands-on classroom environment
- Learn how to exploit and defend real-world web apps: not just silly sample code
- Complete the 83 Step "Web App Pen Test Methodology", and bring a copy back to work with you
- Learn how perform OWASP Top 10 Assessments: for PCI DSS compliance
Network Spoofer is another nice app that lets you change the website
on other people’s computer from your Android phone. Download the Network
Spoofer app and then log onto the Wi-Fi network. Choose a spoof to use
with the app then tap on start. This app is considered as a malicious
hacking tool by network administrators. So, don’t try on unauthorized
networks. This is not a penetration testing app. It’s just to
demonstrate how vulnerable the home network is.
Download this app from sourceforge
http://sourceforge.net/projects/netspoof/
3. Network Discovery
Network Discovery is a free app for the Android device. The good
thing is that the app doesn’t need a rooted device. This app has a
simple and easy to use interface. It views all the networks and devices
connected to your Wi-Fi network. The application identifies the OS and
manufacturer of the device. Thus the app helps in information gathering
on the connected Wi-Fi network.
Download app from Google Play:
https://play.google.com/store/apps/details?id=info.lamatricexiste.network
4. Shark for Root
Shark for Root is a nice traffic sniffer app for the Android device.
It works fine on 3G and Wi-Fi: both network connectivity options. You
can see the dump on phone by using Shark Reader that comes with the app.
You can also use
Wireshark a similar tool to open the dump on the system. So, start sniffing data on your Android device and see what others are doing.
5. Penetrate Pro
Penetrate Pro is a nice Android app for Wi-Fi decoding. The latest
version of the app has added many nice features. It can calculate the
WEP/WAP keys for some wireless routers. If you have installed an
Antivirus app, it may detect Penetrate Pro app as virus. But this app is
a security tool and it will not affect or harm your device.
Penetrate gives you the wireless keys of Discus, Thomson, Infinitum,
BBox, Orange, DMax, SpeedTouch, DLink, BigPond, O2Wireless and Eircom
routers.
6. DroidSheep [Root]
DroidSheep is a session hijacking tool for Android devices. This is
an app for security analysis in wireless networks. It can capture
Facebook, Twitter, and LinkedIn, Gmail or other website accounts easily.
You can hijack any active web account on your network with just a tap
by using the DroidSheep app. It can hijack any web account.
This app demonstrates the harm of using any public Wi-Fi.
Download this app from here:
http://droidsheep.de/?page_id=23
7. DroidSheep Guard
DroidSheep Guard is another Android app that also developed
Droidsheep. This app does not require a rooted device. This app monitors
Android devices’ ARP-table and tries to detect ARP-Spoofing attack on
the network performed by DroidSheep, FaceNiff and other software.
Download DroidSheep Guard from Google Play:
https://play.google.com/store/apps/details?id=de.trier.infsec.koch.droidsheep.guard.free&feature=search_result
8. WPScan
WpScan is the WordPress vulnerability scanner for Android devices.
This nice app is used to scan a WordPress based website and find all the
security vulnerabilities it has. WPScan also has a desktop version of
the app that is much powerful than the Android app. We know that
WordPress is one of the most popular CMS and is being used by millions
of websites.
The Android version of the app comes with few nice features. The app
was released on Google Play but Google removed the app. The full source
code of the app is available from Github. One thing to note that WPScan
Android app is not related to the desktop version of WPScan. So, never
think it as an official WPScan app.
Download app and source code:
https://github.com/clshack/WPScan
9. Nessus
Nessus is a popular penetration testing tool that is used to perform
vulnerability scans with its client/server architecture. It also
released its mobile app to bring its power on mobile devices. Nessus
Android app can perform following tasks.
- Connect to a Nessus server (4.2 or greater)
- Launch existing scans on the server
- Start, stop or pause running scans
- Create and execute new scans and scan templates
- View and filter reports
This app was released on Google Play store almost 2 years back by
Tenable Network Security. Later Google removed the app from Play store.
Now the official link has been removed. So you can try downloading links
available on third party websites. But be careful and check the app
first.
10. FaceNiff
FaceNiff is another nice sniffing app for Android devices. It
requires a rooted Android device. It can sniff and intercept the web
sessions over the Wi-Fi. This app is similar to DroidSheep, added
earlier in the post. You can also say Firesheep for Android devices. Use
of this app may be illegal in your area. So, use it wisely.
11. WebSecurify
WebSecurify is a powerful web vulnerability scanner. It’s available
for all popular desktops and mobile platforms. It has a powerful crawler
to crawl websites and then attack it using pre-defined patterns. We
have already covered it in detail in our previous article. You can read
the older article for better understanding.
Download it here:
https://code.google.com/p/websecurify/
12. Network Mapper
Network Mapper is a fast scanner for network admins. It can easily
scan your network and export the report as CVS to your Gmail. It lists
all devices in your LAN along with details. Generally, the app is used
to find Open ports of various servers like FTP servers, SSH servers, SMB
servers etc. on your network. The tool works really fast and gives
effective results.
Download Network Mapper for Google Play Store:
https://play.google.com/store/apps/details?id=org.prowl.networkmapper&hl=en
13. Router Bruteforce ADS 2
If you are connected to a wi-Fi network and you want to access the
router of the network, you can use Router Bruteforce ADS 2 app. This app
performs Bruteforce attack to get the valid password of the router. It
has a list of default passwords that it tries on the router. Most of the
time, the app cracks the password. But you cannot be 100% sure in
Bruteforce attack.
It comes with a sample txt file which contains 398 default passwords
used in different routers. You can add more passwords in the list. But
there is one limitation. This app only works with dictionary file of
less than 5 MB. And try it only when you have good Wi-Fi signal. This is
an experiment app and the developer also warns users to try at own
risk.
Download Router Bruteforce ADS 2 from Google Play:
https://play.google.com/store/apps/details?id=evz.android.rbf_ads&hl=en
14. Andosid
AnDOSid is another nice application that can be used to perform DOS
attacks from Android mobile phones. It is like LOIC tool for desktop. In
the app, you can set target URL, payload size and time difference
between two requests. After that click on big GO button to launch DOS
attack on a website. It will start flooding target URL with fake
request. Use this app if you have a powerful device. Avoid if you have
low cost entry level device.
15. AppUse – Android Pentest Platform Unified Standalone Environment
AppUse Virtual Machine is developed by AppSec Labs. It’s a freely
available mobile application security testing platform for Android apps.
This android penetration testing platform contains custom made tools by
AppSec Labs.
This penetration testing platform is for those who are going to start
penetration testing of Android applications. All you need is to
download the AppUse Virtual Machine and then load the app for testing.
The app comes with most of the configuration. So, you do not need to
install simulators, testing tools, no need for SSL certifications of
Proxy. Thus, the tool gives ideal user experience. In other words, you
can say that AppUse Virtual Machine is Backtrack for Android apps. As we
know that world is moving towards apps, AppUse VM has a good scope in
future. We see how Android users face attacks and these cyber-attacks
are growing. So, it is important for all Android app developers to test
their apps for various kinds of vulnerabilities.
Download AppUse Virtual machine Here
http://sourceforge.net/projects/appuse-android-pentest/files/AppUse%201.6_release.rar/download
Conclusion
Android is one of the fastest growing mobile platforms with the
biggest market share. People also claim that it could replace desktop OS
as well. Although we do not agree with that but, we cannot ignore the
importance of it. This is why developers are bringing their tools for
Android platforms also. In this post, I have listed few Android apps for
hackers and security researchers. You can say that these apps are not
as powerful as desktop hacking tools. But you can still enjoy these
hacking tools for most of your tasks. Most of the hacking apps are
related to networking and spoofing. All these apps do this task on
Wi-Fi. Few web scanners are also available that lets security
researchers find vulnerability on web applications.
You can also launch DOS attack on a website direct from your smartphone or tablet. This could be a better hacking tool.
If you are into the security field, you can try these apps and see how these work